Title: Ethereum: Zk Rollups – Security Under Threat
Introduction
The Ethereum network has long been considered one of the most secure and decentralized blockchain platforms available today. Its innovative use of zk-rollups, a cutting-edge concept in cryptocurrency transactions, has made it an attractive choice for users seeking to maintain their privacy and control over their financial data. However, as with any technology, vulnerabilities can exist.
Zk Rollup’s Zk-Snark Proof System
zk rollups rely on the security of zk-snark, a zero-knowledge proof system developed by Oded Maler and Guy Sussman in 2016. This concept allows for the verification of transactions without revealing their contents, thereby maintaining user privacy.
The process involves breaking down complex transactions into smaller, verifiable pieces called “block chunks.” Each block chunk is then verified by a network of nodes, ensuring that all transactions within the block are legitimate and have not been tampered with. Once verified, the block chunks are combined to form a single block, which is then added to the Ethereum blockchain.
The Vulnerability: Malicious Relayer’s Proof Using Incomplete Transactions
Now, consider the scenario where a malicious relayer creates a proof using incomplete transactions in a batch (e.g., 10+ transactions with empty inputs). This malicious action would allow them to create a false narrative about the state of their blockchain. To achieve this:
- Batching: The malicious relayer bakes multiple blocks containing different sets of incomplete transactions.
- Proof Generation: They generate a proof using zk-snark that links these batches together, creating the illusion that all valid transactions are included in the batch.
- Relaying: The malicious relayer relays this proof to other nodes on the network, making it appear as though all transactions have been verified.
Security Risks and Consequences
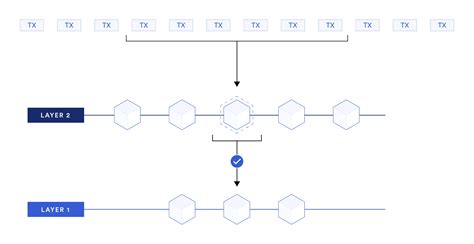
By generating a false-proof of the state transition, the malicious relayer gains several benefits:
- Increased Resilience: If one node or group of nodes fails to verify the transaction, they can still accept the proof and add it to their local copy of the blockchain.
- Reduced Detection Risk: The use of incomplete transactions makes it more difficult for validators to detect malicious relaying.
However, this strategy also poses several risks:
- Increased Attack Surface: By making it easier for malicious actors to create false proofs, the overall security posture of the network is compromised.
- Network Segregation: As more nodes fall victim to the malicious relayer’s scheme, the blockchain’s integrity may be disrupted, potentially leading to a breakdown in network segregation.
Mitigation Strategies
To address these vulnerabilities, several measures can be implemented:
- Blockchain Segregation
: Implementing segregation of concerns (SoC) techniques and smart contract-based isolation mechanisms can help prevent malicious actors from compromising critical components.
- Improved Network Monitoring: Enhancing node monitoring and anomaly detection capabilities can identify potential threats more efficiently.
- Smart Contract Auditing: Regularly auditing and testing smart contracts for vulnerabilities can help mitigate the impact of successful attacks.
By acknowledging these risks and implementing effective mitigation strategies, Ethereum developers can work towards creating a more secure and resilient zk-rollup-based network that balances user privacy with the need for robust security measures.